Superna Data Security Edition
Protect your file and object data from cyberthreats
Superna’s Data Security Edition is a highly scalable, real-time event processing solution that employs user behavior analytics to detect and halt ransomware and other cyberattacks. By monitoring user file system access, Superna detects changes to normal data access patterns, and can take defensive action to prevent major damage and minimize recovery time.
Inadequate monitoring and protection at the storage layer leaves your data vulnerable to ransomware and exfiltration. Superna’s advanced, real-time monitoring, along with early-stage detection mechanisms, highlights behavioral changes and potential threats, locking them down to minimze impact to your business operations.
Security Edition Highlights
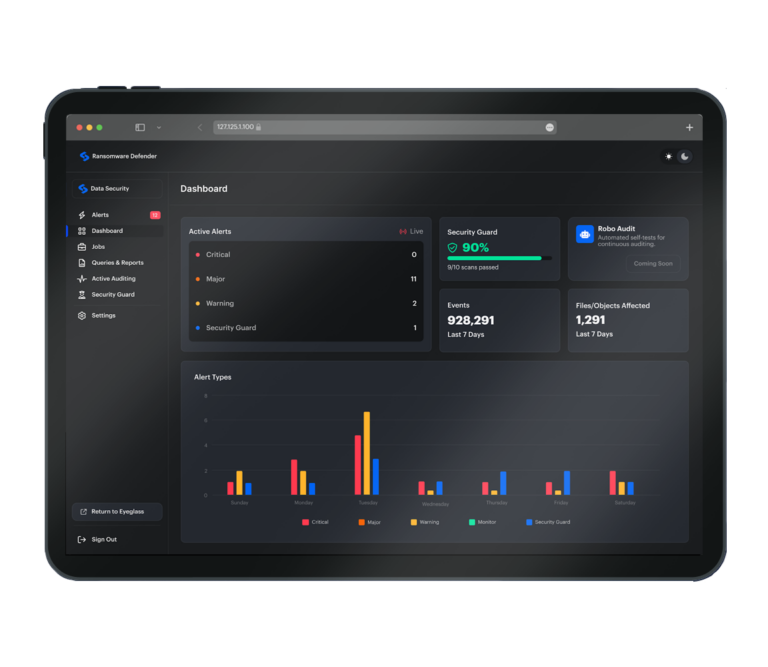
- Real-time detection of cyberthreats on file and object data
- Quickly identifiy and shut down bad actors
- Monitor and report on anomalous activity
- Automated false positive detection learns from expected behaviors
- One-click recovery from previous unaffected snapshots
- File auditing for analysis and compliance
- Active auditing with real-time security audit triggers
- Zero-Trust API for seamless 3rd-party integrations
- Optional AirGap (sold separately) for enhanced security and recoverability


Data protection at the storage layer
With Superna, you can defend against security threats, protecting data from leakage, ransomware, and cyberthreats. By focusing on a “data first” strategy, Superna’s tools for security, analytics and protection can help you reduce risk and achieve better business results.
Highlighted Features
 Feature
Feature
Where Did My Folder Go? feature can be used to quickly and easily find where a folder went, who moved or deleted it and at what time, or where a file went, who moved or deleted it and at what time
 Feature
Feature
Wiretap can be used to monitor all IO to a path or a user for debugging, security monitoring, or excess permissions to a path, share or export
Real-time threat detection, alerting, and attacker lockout
Widest platform support of any cyberstorage vendor
- Enables snapshots and lockouts across supported platforms to ensure protection and recoverability of your critical data.
- Easily monitor multiple production clusters from a single user interface.
- Real-time analytics help pinpoint possible threats and trigger appropriate response.
- Real-time monitoring allows for a preview of user actions, enabling informed decision-making.
- Native integrations with leading SIEM and SOAR platforms streamline workflows and allow you to monitor and manage your data theorugh your preferred user interface.
Create your own triggers to get alerted and have snapshots taken when:
Speak To An ExpertSpeak To An Expert Today
Speak To An Expert today to learn more about how Superna’s Data Security Edition can protect your most valuable file and object data from cyberthreats.