Threat Hunting
Stop ransomware before it starts.
Your biggest blind spot isn’t at the perimeter—it’s inside your file shares. Superna Threat Hunting uses AI-powered anomaly detection to identify ransomware reconnaissance and insider threats before they strike.
Traditional tools — like firewalls, endpoint agents, and SIEMs – weren’t designed to monitor activity within your file shares.
That blind spot is where attackers quietly operate: mapping directories, copying sensitive files — executing data exfiltration enabling double extortion — often without triggering a single alert.
They steal data to hold for ransom even if encryption is detected or rolled back.
Storage wasn’t built with security in mind, and the gap between storage and security teams leaves organizations exposed to silent, high-impact breaches.
Storage admins aren’t equipped to review every file access alert. Security teams, meanwhile, often lack file-level context. This creates:
Data Layer Visibility Gaps:
Extended dwell time:
Delayed detection:
Storage-Security Gap:
Superna Threat Hunting closes this gap with AI-driven anomaly detection for unstructured data.
By continuously monitoring user file activity, the system learns what “normal” looks like—and flags unusual deviations that may signal ransomware reconnaissance, insider compromise, or other early-stage malicious activity.
Confidence Scoring
high-risk anomalies prioritized, noise reduced
On-Premises Processing
ensures data privacy and sovereignty
SIEM/SOAR Integrations
plug into 50+ platforms (Splunk, CrowdStrike, ServiceNow, Microsoft Defender, SentinelOne, and more)
Automated Workflows
contextual file access data flows directly into your security processes
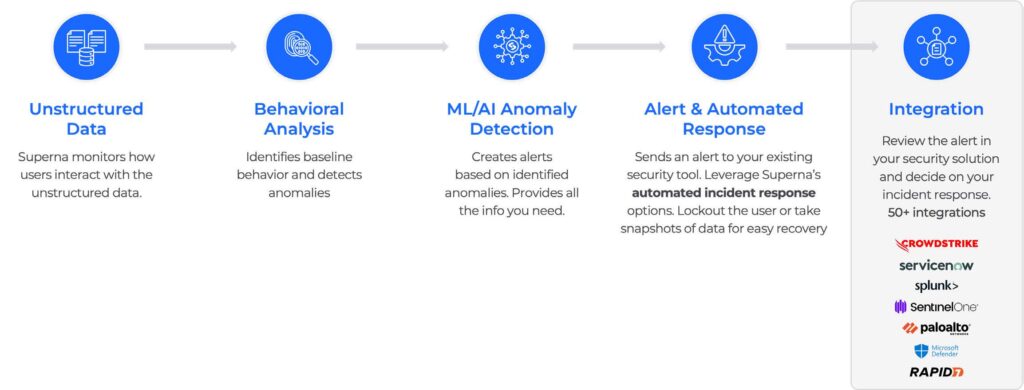
Superna Threat Hunting gives security teams the intelligence they need—without burdening storage admins.
This is storage-level cyber resilience—a critical new layer recognized by Gartner in its Innovation Insight for Cyberstorage report.
Detect ransomware reconnaissance and insider threats before encryption or theft
Cut attacker dwell time, limiting their ability to access, collect, or exfiltrate data
Reduce Mean Time to Detect (MTTD) with real-time anomaly insights
Minimize alert fatigue with prioritized, high-confidence alerts
Correlate file anomalies with broader security intelligence
With Superna Threat Hunting, you’ll: